IoT
We enable organizations to manage digital identities and control user access to critical corporate information
Pain points
IoT devices are easy targets for hacking and targeted malware. When exposed to these attacks, IoT devices are prone to large-scale information leakage or accidents.
- Weak and predictable passwords
Most IoT devices come with a password set in advance when shipped from the factory, leaving some users easily exposed to risk as a result of not updating the password. Even if you change your password, this static code becomes an easy game for hackers.
- Unsecured network services
Devices connected to networks communicate continuously amongst themselves using various wireless communication protocols. Such communication guarantees the response of IoT applications, but if it becomes infected by malicious code or hijacked by a low-security wireless protocol, this poses a real cause for concern. Numerous IoTs, such as radio-controlled aircraft, radio-controlled cars, and industrial drones, have the potential of being hijacked. A private network can completely separate the internal network from the external, providing the most secure environment for IoT, yet it costs a fortune to build and operate such a dedicated network. A virtual private network (VPN) could be a cheaper option than a private network, but it also requires a lot of implementation and management costs so, may not be so cost-efficient.
- Improper data transmission
The onboard chip used for communication between the telemetry module and the unmanned device mainly uses a low-security wireless protocol. So any sophisticated hacker who can reverse engineer the software on an unmanned device can send navigation controls, block all commands from real operators, or even crash them.
- Limitations of security/authentication solutions to IoT devices
There are many ways to defend against the increasing IoT security threats. However, most IoT devices - e.g., meters, sensors, valves, etc. - are tiny simple devices with low hardware performance, which makes it difficult to continuously operate Transport Layer Security (TLS) or Public Key Infrastructure (PKI) stack. TLS and PKI require a relatively high hardware capacity because of its high memory usage, high power consumption, and heat generation of devices such as PCs and smartphones.
Solutions
IoT security strategies should reduce vulnerabilities by using policies such as device identity management, encryption, and access control. SSenStone provides a safe IoT communication environment by making it impossible to hack and take control of a device through a random code that changes every time in connection and commands.
- Provide unidirectional code generated by the client without communication with the server
- Generate a dynamic code that changes every time and is safe from hacking and leakage
- Block attacks in advance with one-time code that does not allow cloning and spoofing attacks
- Protect devices by issuing a unique code that never overlaps with other connected devices
- With the size of 10KB, OTAC Applet can be installed on all types of SIM Cards(Classic SIM, eSIM, and iSIM)
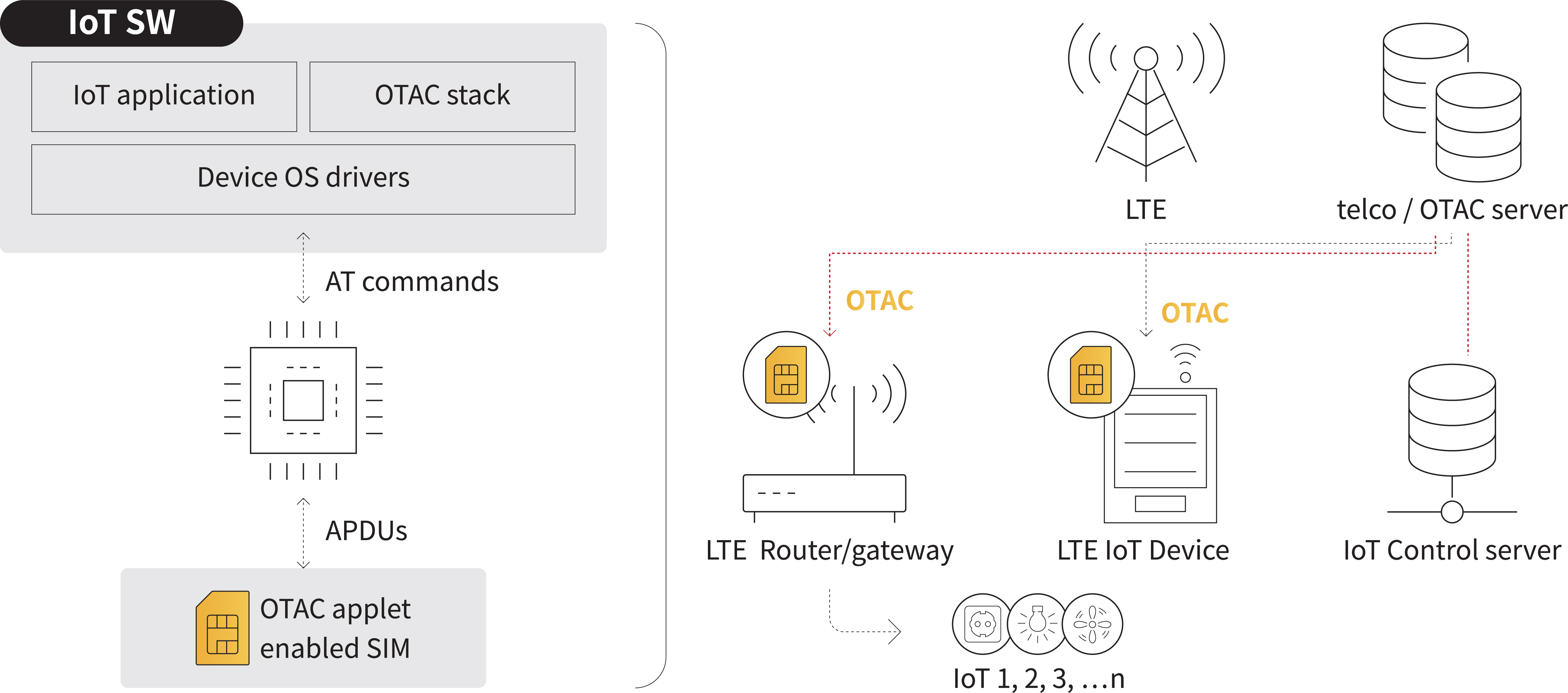
IoT Security Platform - OTAC Applet on SIM Card
Instead of upgrading the firmware of each of numerous heterogeneous IoT devices, because the OTAC applet is applied to the SIM card, it increases the efficiency of integration and deployment. Also, it can be applied to low-capacity devices that are usually difficult to continuously operate TLS or PKI stacks. In addition, it can also minimise memory usage and power consumption.
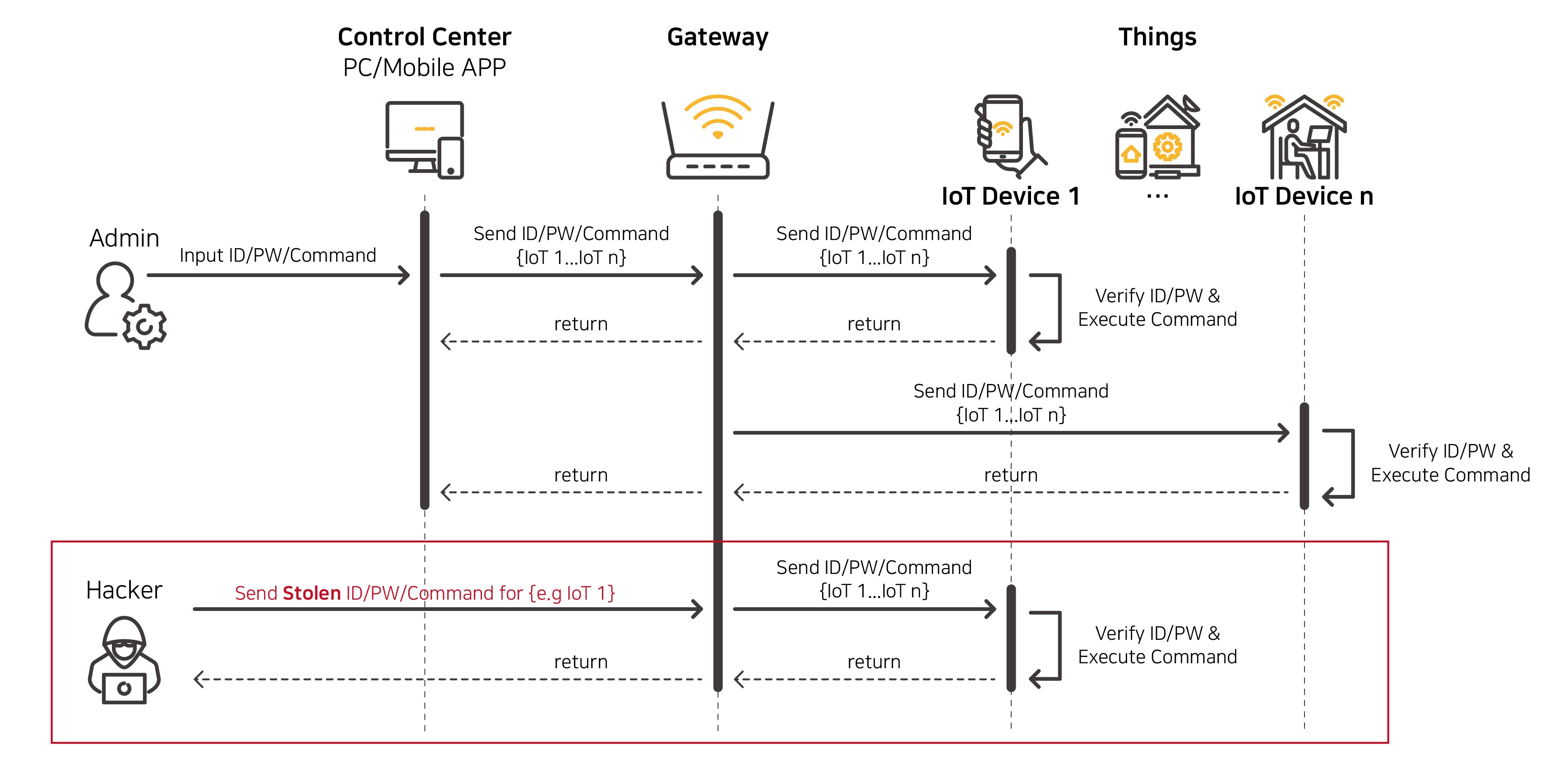
[AS-IS]
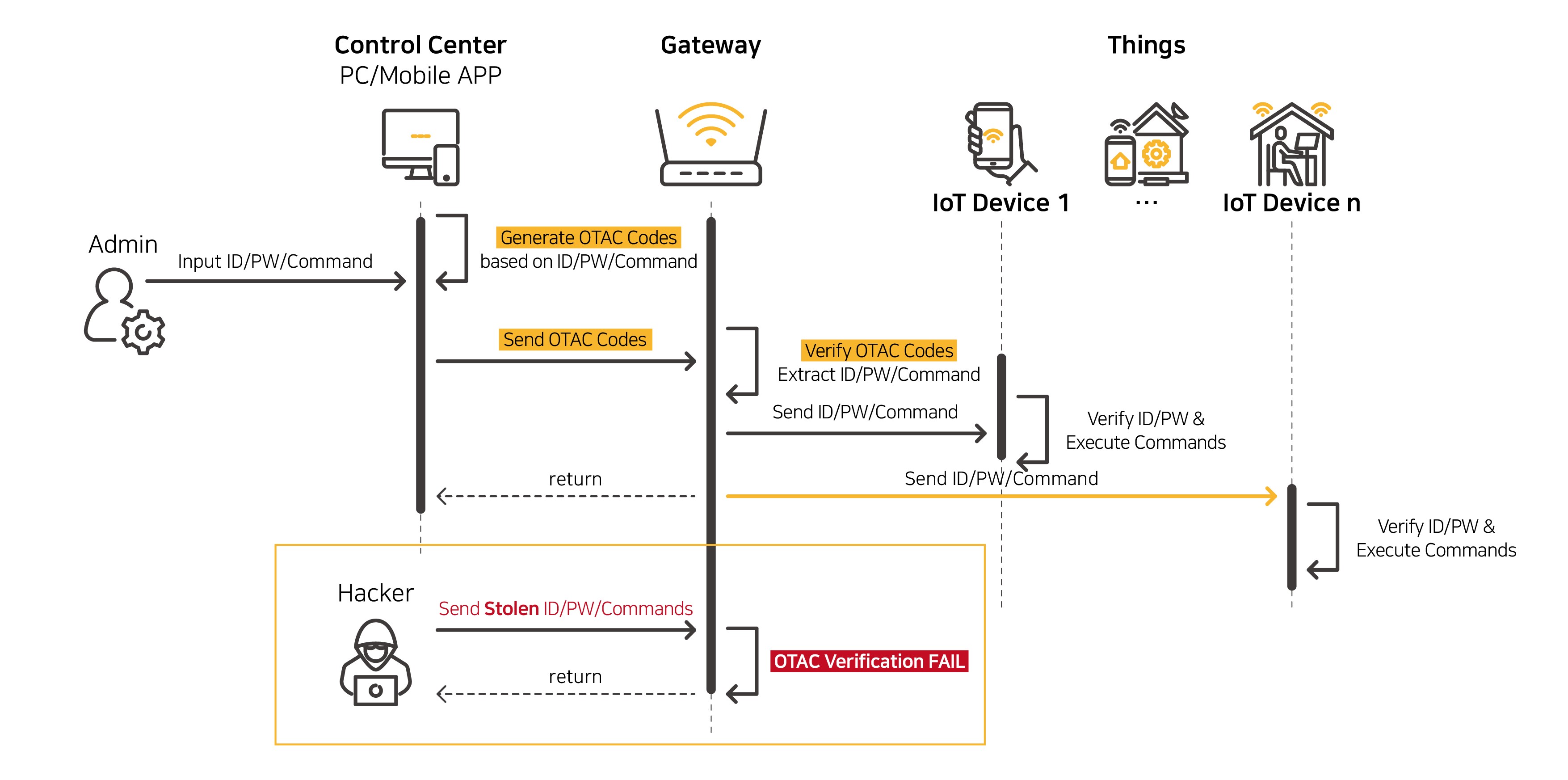
Looking at the most common configuration of IoT systems, there are two problems in Device Control & User Authentication.
- ■ Static value or unencrypted plaintext are used in most of the command delivery.
- ■
Without a verification process between server and the device, any received information could be transmitted to the IoT device as it is, without being checked whether it is from legitimate control server. Therefore, when command information is stolen by any chance, IoT devices can be easily controlled by unauthorized systems (hackers).
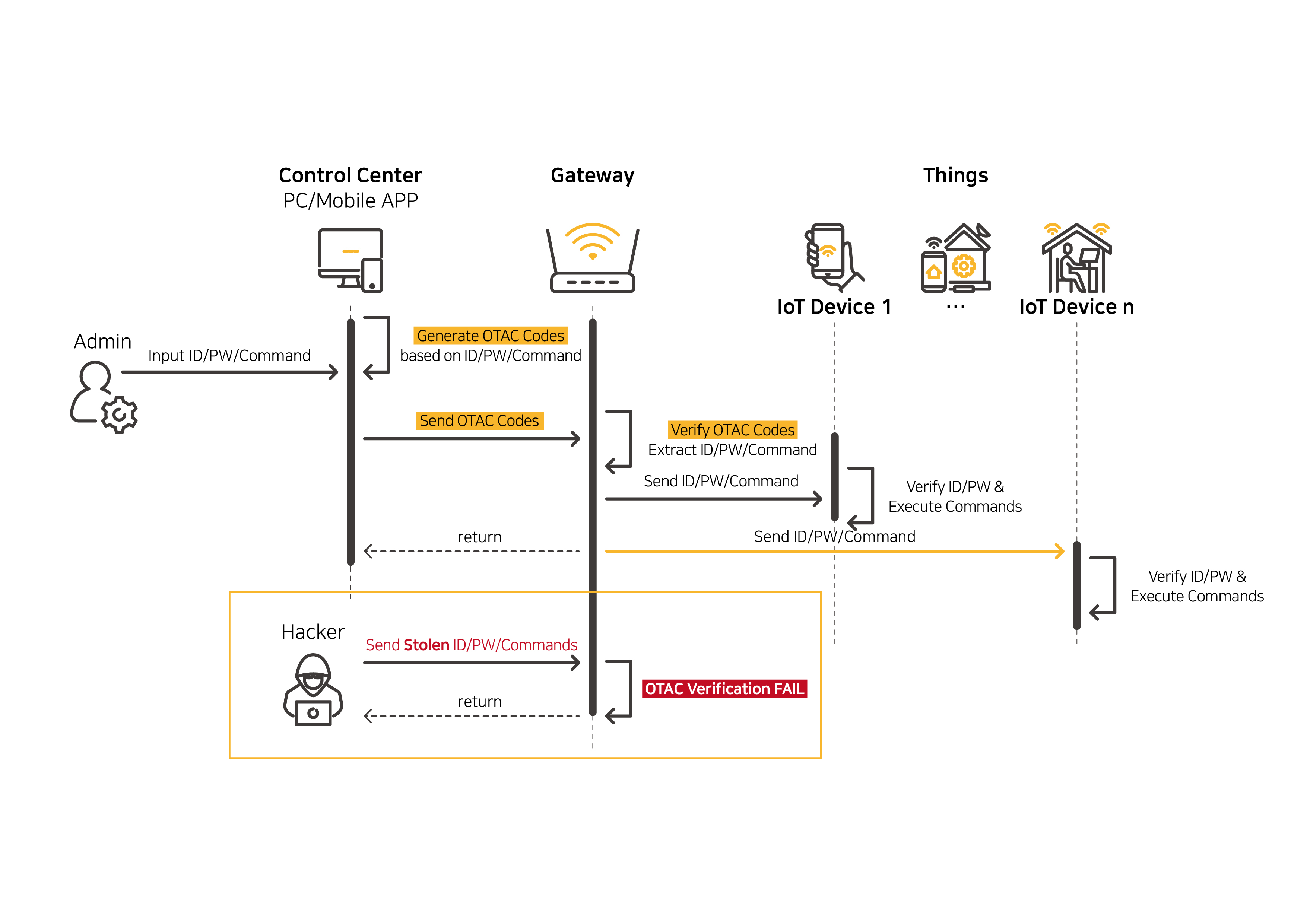
[TO-BE]
You can expect more security when verification is performed on SIM card with OTAC (One Time Authentication Code) Applet applied.
- ■ When the control server sends commands to the LTE gateway, it generates and sends OTAC.
- ■
The commands that have passed OTAC SIM verification can only be delivered to IoT devices, preventing the problem of any commands being delivered to devices as they are. Due to the nature of OTAC which is valid only at one time, continuously changing dynamically, even if a hacker steals the OTAC, it cannot be reused.
[AS-IS]
Looking at the most common configuration of IoT systems, there are two problems in Device Control & User Authentication.
-
■ Static values or unencrypted plaintext are used in most of the command delivery.
-
■ Without a verification process between the server and the device, any received information could be transmitted to the IoT device as it is, without being checked whether it is from a legitimate control server. Therefore, when command information is stolen by any chance, IoT devices can be easily controlled by unauthorized systems (hackers).
[TO-BE]
You can expect more security when verification is performed on SIM card with OTAC (One Time Authentication Code) Applet applied.
-
■ When the control server sends commands to the LTE gateway, it generates and sends OTAC.
-
■ The commands that have passed OTAC SIM verification can only be delivered to IoT devices, preventing the problem of any commands being delivered to devices as they are. Due to the nature of OTAC which is valid only at one time, continuously changing dynamically, even if a hacker steals the OTAC, it cannot be reused.
DRONE
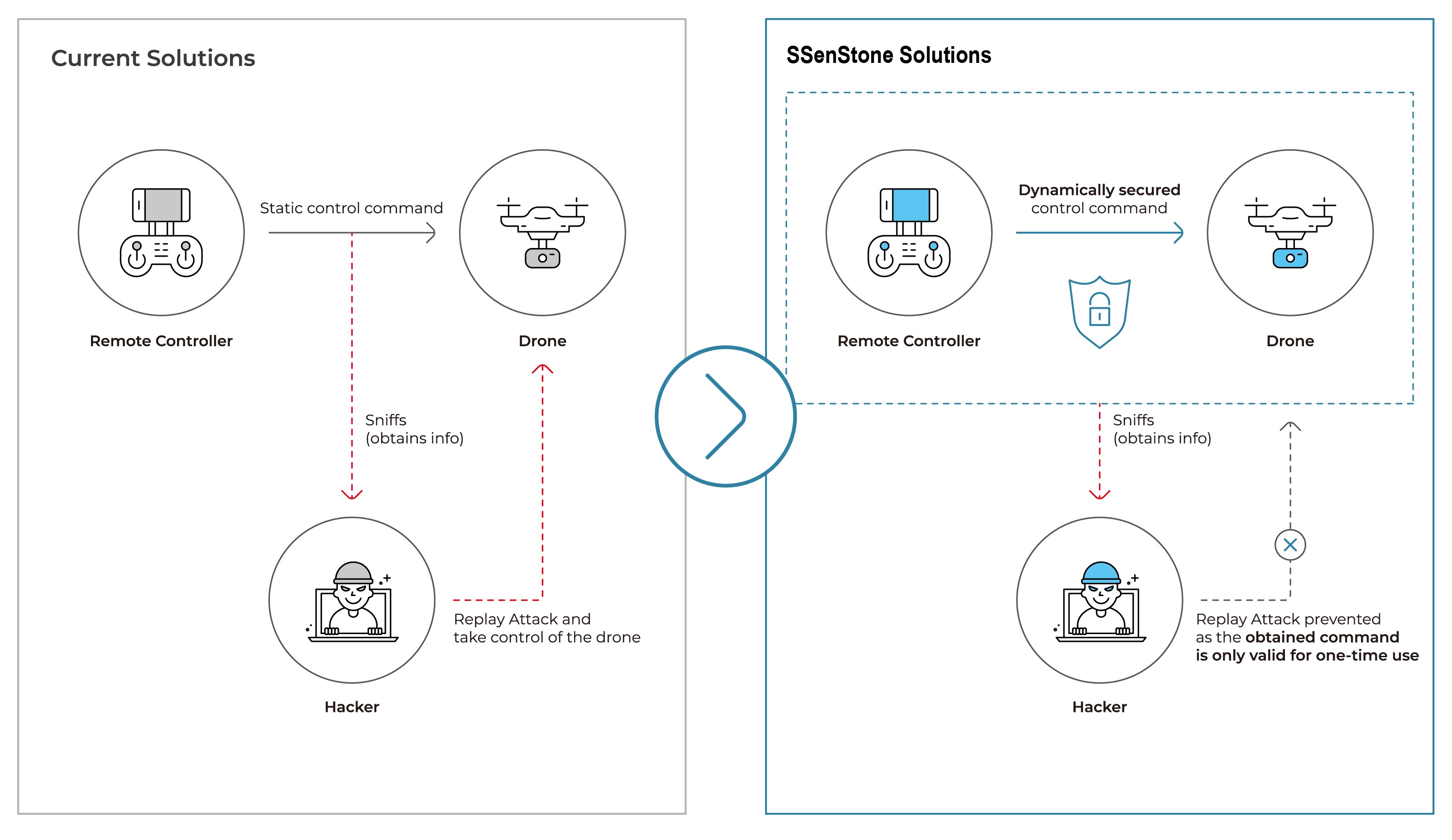
OTAC on Drone Remote Control System
Through OTAC, pilots can safely access the drone remote control system, and all commands from the remote control system and controller are converted into one-time dynamic codes and sent to the drone. This makes it impossible for any external intruders to steal and control the drone as the command is no longer valid. The command converted into dynamic code can solve the risk of hijacking such as protocol tampering attack and replay attack.
AI Speaker
AI Speaker Login & Payments
AI Speaker Login & Payments
Users can easily identify themselves by calling the one-time authentication code of SSenStone, which changes every time, anytime, anywhere, to the AI speaker. It is possible to expand the AI speaker technology and ecosystem based on safe authentication from pairing with IoT devices such as vacuum cleaners, televisions, refrigerators, and shopping to payment.
.png)
OTAC는 통신 네트워크가 없는 상황에서도 IFF가 고유한 다이내믹 코드를 생성하고, 생성값을 인증하여, 단방향으로 간편하게 타깃을 식별할 수 있도록 하는 혁신적인 인증 기술입니다. OTAC 기술을 활용하여 생성된 단방향 다이내믹 코드는 아군 식별 및 적의 신호 도용 방지에 적용됩니다.
Why OTAC
OTAC, developed by SSenStone, is the original technology that provides all of the following features at the same time.
-
OTAC is a dynamic code, which means the code keeps changing. As a result, you don’t need to worry about any leak of your personal information, such as your card details, because the codes must have already been changed when others try to use them.
-
The network connection is NOT necessary at all for generating OTAC.
Reducing an authentication stage that requires the network connection directly means there are fewer gateways for the hackers to access our personal information.
Moreover, this feature enables users to authenticate even when they are in networkless environments, such as on the plane, underground, rural or foreign areas. -
swIDch can guarantee that the code never duplicates with anyone at any given moment.
There is NO chance of someone else having the same code. -
The users or their devices can be identified with the code alone.
Once OTAC has been generated, providing OTAC alone is already fully sufficient to identify the user as the code is unique.
It means, you can forget about the bundles of static information including IDs and passwords.

